Simplifies boundary security architecture, mainly used at key network entry points in the internet and data centers to support unified deployment of security tools.
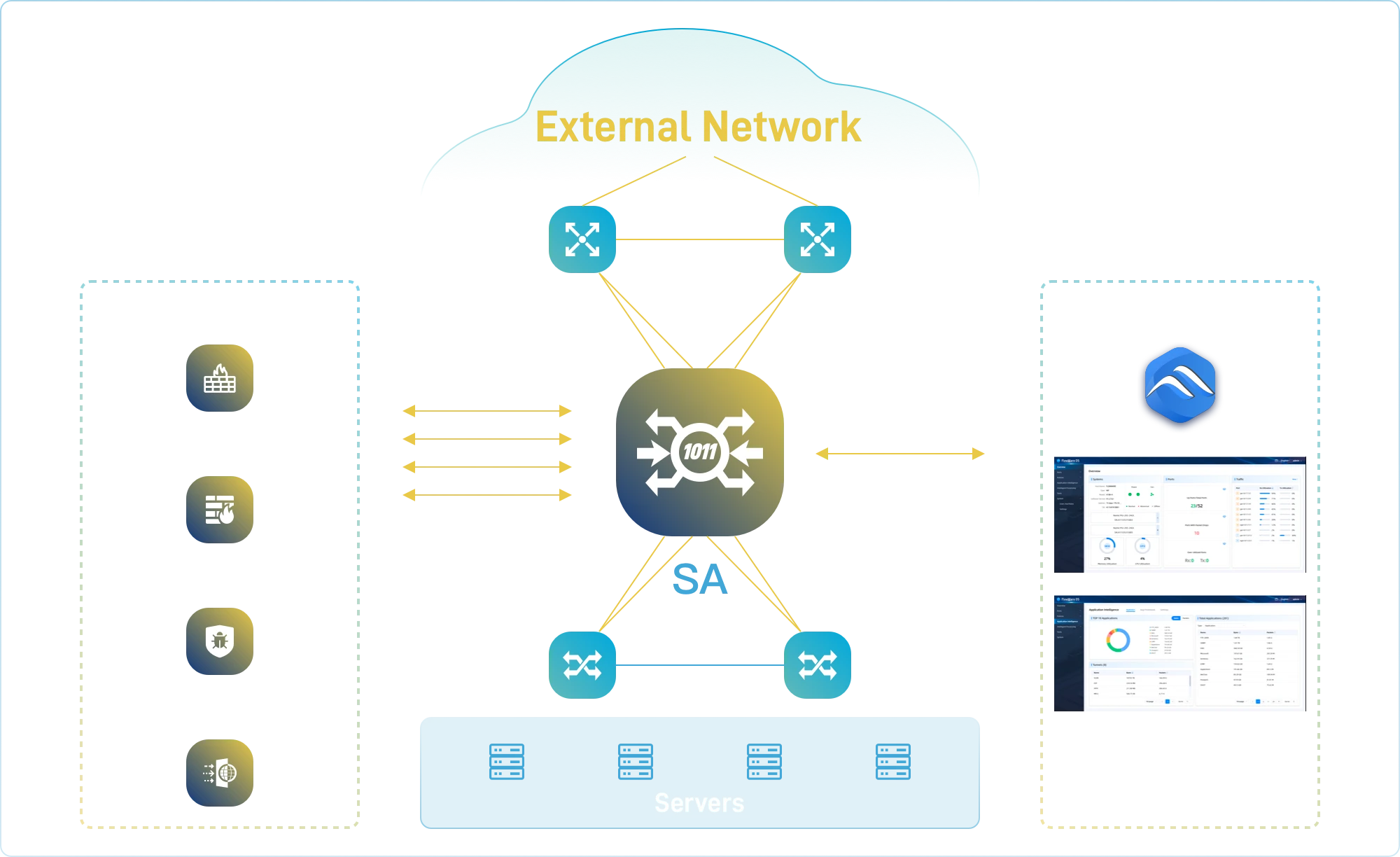
- Traffic Steering
❖ Supports plug-and-play of security tools with flexible sequence definition.
- Traffic Orchestration
❖ L2-L7 orchestration capabilities to enhance tool efficiency.
- Tool Resource Pooling
❖ Resource pooling improves utilization and protects investments.
- SSL Offloading
❖ Single decryption for multiple uses, reducing latency.
- High Availability
❖ Built-in BYPASS and health monitoring ensure uninterrupted networks.
- Visual Operations
❖ Centralized management simplifies network observation.
- Maximized Network Availability
Simplified access reduces faults; BYPASS ensures continuous protection.
- Maximized Operational Efficiency
Flexible tool deployment and upgrades with easy management.
- Maximized Tool Effectiveness
Traffic filtering alleviates overload, enhancing network performance.