With the booming development of the digital economy , APIs , as the "portal" for data exchange , carry the core business logic of information systems in various industries and are an important channel for transmitting data . In recent years, they have attracted the attention of attackers in the black and gray industries and have become a disaster area for data leaks. At the same time, the increasingly stringent national regulatory laws and compliance requirements have further highlighted the urgency of API security issues. Therefore, organizations urgently need to attach great importance to API data security and actively explore effective risk mitigation strategies.
- API asset agnostic
How much is the total API
the API status?
Are there any connections between APIs?
Is the API sensitive?
- API risks are undetectable
the API have any security flaws?
the API have any security vulnerabilities?
Is there any risk in the access behavior?
Is there any risk in data transfer ?
- API access is not traceable
Who accesses sensitive APIs?
When are sensitive APIs accessed?
Data flow cannot be traced Illegal calls cannot be traced
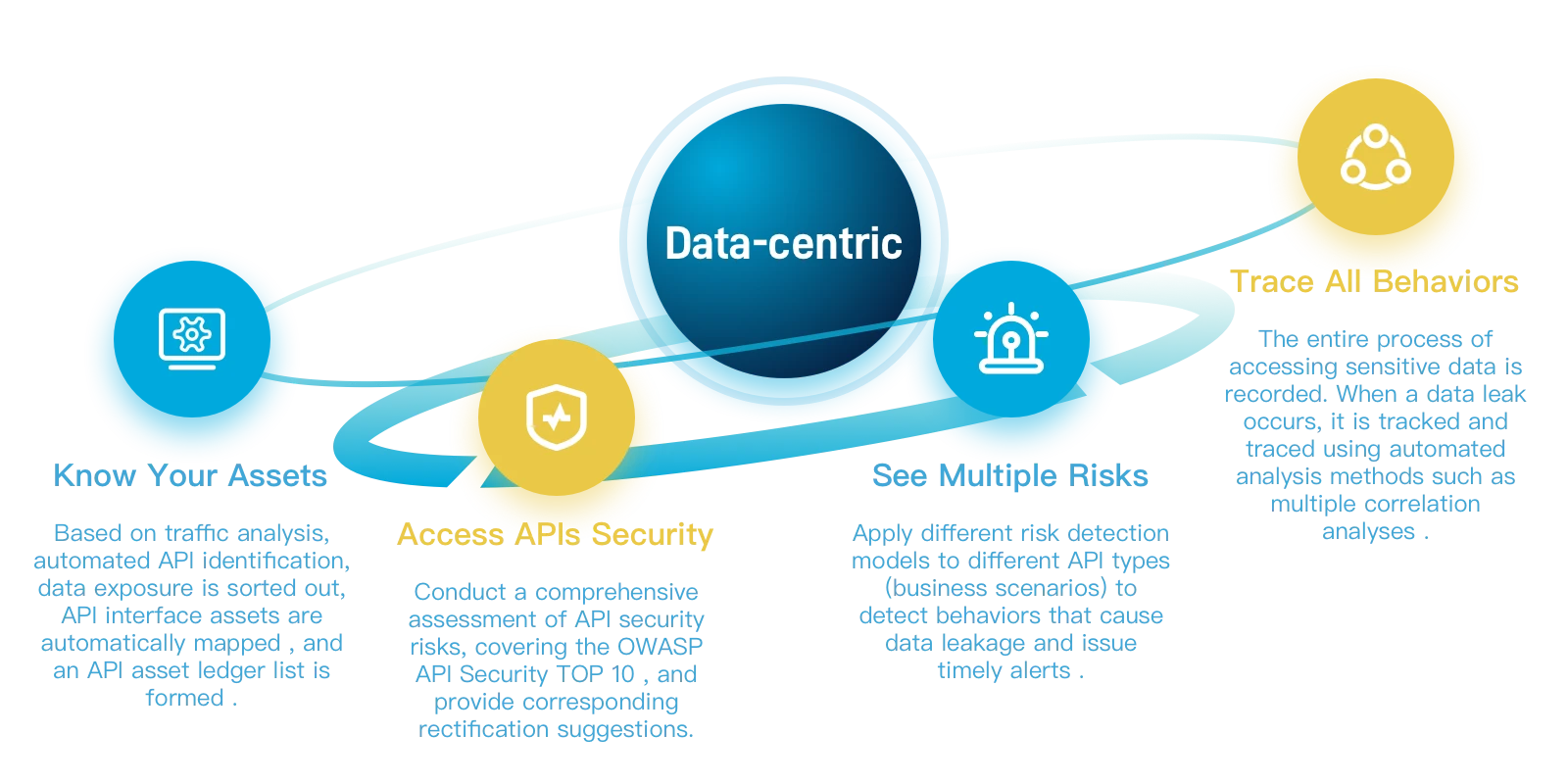
Sinosig API Security Risk Monitoring System is an intelligent security solution designed to cope with the current complex API security threats. Based on traffic analysis and data identification technology, it uses a "four-step" strategy - API assets can be known, hidden dangers can be assessed, risks can be observed, and access behaviors can be traced . It monitors the exposure and attack status of API data within the organization in real time , ensures timely discovery and response to security incidents, and guarantees data security and stable business development . | ||||
| ||||
at data does the API expose? Identify and label API exposure surface including exposed data and exposed network segments Sort out the latest API list Dynamically and real-timely sort out the API list to catch zombie APIs and shadow APIs How sensitive data flows Identify sensitive data transmitted in APIs and monitor the flow of business data |
| Conduct Risk Monitor API operation compliance behavior risks including cross-border out-of-domain abnormal batch download etc Vulnerability risk:API vulnerabilities Monitor high-risk API attacks such as injection and crawling Vulnerability risk:OWSAP TOP10 Identify issues covered by OWASP API Security TOP 10 | ||
API operation leave comprehensive traces Record all API operation behaviors and support fast scenario- based tracing | ||||
- Wide coverage Multi- dimensional API Asset Management
It covers multiple API formats, data formats, multiple data tags, API types, risk models, and supports intelligent API asset sorting and identification.
- Flow Visibility Visual data flow management
Automatically sort out data flow paths, conduct data flow heat analysis and data statistical analysis, and assist in data flow risk monitoring.
- AI Empowerment Intelligent security analysis and protection
Intelligent threat identification, hidden danger feature interpretation and risk prediction, and adaptive security strategy optimization to achieve accurate and efficient security protection.
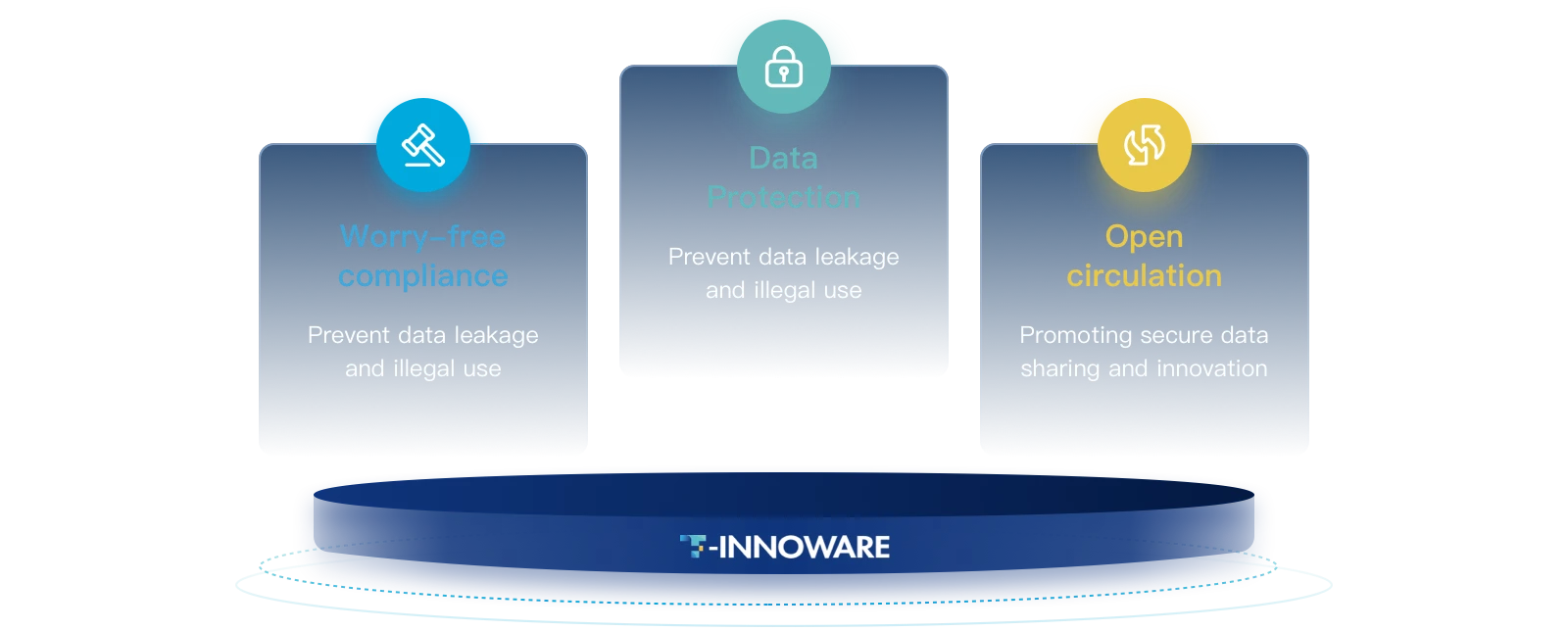
Sinosig API Security Risk Monitoring System provides enterprises withcomprehensive value from compliance management to data security to businessinnovation, helping enterprises to effectively respond to API security challenges,promote the stable development of business, and truly achieve a win-win situation forbusiness and security |
|